With breaches making the headlines on an almost weekly basis, the cybersecurity challenges we face are becoming visible not only to large enterprises, who have built security capabilities over the years, but also to small to medium businesses and the broader public. While this is creating greater awareness among smaller businesses of the need to improve their security posture, SMBs are often left facing a gap in the market, unable to find security tooling that is both easy for them to use and which they can afford.
When we consider the needs of SMBs, we need to focus both on the development of threat intelligence, which is necessary to understand and identify the threats being faced, as well as the tools used to provide protection. NTTSH has built a pedigree of over 20 years’ experience in the research and curation of threat intelligence as well as the development of capabilities and products which leverage its threat intelligence to protect customers. After many years of focus on larger enterprises, NTTSH is moving to democratize cybersecurity and provide smaller businesses with the protection they require.
Global Threat Intelligence Center
All of NTTSH’s efforts are underpinned by the capabilities of its Global Threat Intelligence Center (GTIC). The efforts of the GTIC go beyond those of a pure research organization by taking threat research and combining it with NTTSH proprietary detective technology to produce applied threat intelligence.
The GTIC’s mission is to protect clients by providing advanced threat research and security intelligence, enabling NTTSH to prevent, detect, and respond to cyber threats. To provide a truly unique vantage point within NTTSH’s products and services, GTIC leverages proprietary intelligence capabilities and NTT’s position as the operator of one of the world’s top 5 tier 1 Internet backbones, providing unequaled visibility of Internet telemetry to gain an understanding of and insight into the various threat actors, exploit tools and malware – and the tactics, techniques, and procedures used by attackers. In addition to curating its own threat intelligence research, GTIC also maintains relationships with other key players in this space, including the Cyber Threat Alliance, Microsoft, CISA, and the National Cyber Forensics and Training Alliance (NCFTA).
NTTSH’s annual Global Threat Intelligence Report (GTIR) provides a window into the work done by GTIC, providing a synopsis of the key challenges in the security landscape facing organizations of all sizes, together with actionable insights to help organizations better adapt to the evolving threat landscape. In the Q3 update of the 2023 GTIR, a special focus was placed on key industry verticals, providing insights into the threats they face.
Threat focus by sector
The healthcare sector faces a unique set of challenges, not only due to the high value of the information owned by healthcare providers but also as a result of steep growth in the adoption of technology in healthcare in a context where many providers, especially smaller ones, lack awareness of cybersecurity and also don’t have the resources to deploy and maintain the kinds of controls enjoyed by large enterprises. Ransomware is still proving particularly problematic. Healthcare ransomware breaches are proving to be particularly concentrated across a few geographies, with the USA, Australia, and the UK accounting for close to 80% of these breaches.
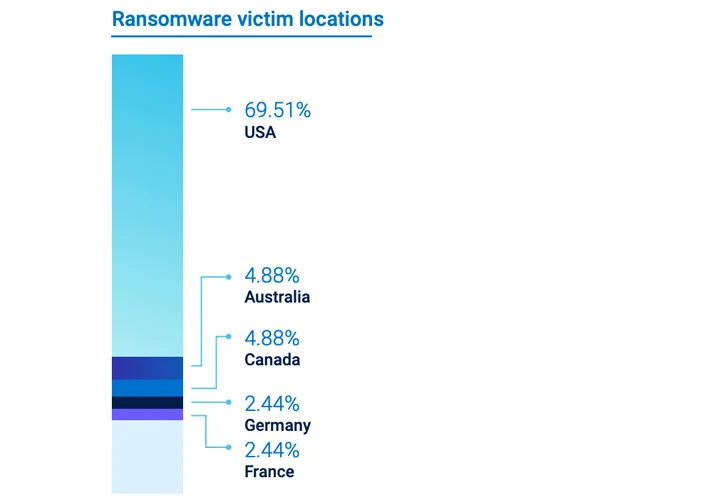 |
| Figure 1: Ransomware victim locations in the Healthcare sector. |
A similar geographic trend is visible in the telecommunications sector, where the USA, UK, and Australia account for roughly 52% of ransomware attacks, while in education, the USA, UK, and Canada account for approximately 83%.
Across all of the focus sectors, Lockbit 3.0 remains the most prolific ransomware threat actor. Some ransomware actors are, however, focusing on specific sectors, such as the Bl00dy ransomware gang, which specifically targets education.
 |
| Figure 2: Top ransomware actors in the telecommunications sector |
Security Challenges of SaaS
A recent area of focus for GTIC has been the way in which the rapidly accelerating adoption of SaaS is presenting its own set of challenges. SaaS is rapidly becoming an integral part of the day-to-day operations of both small and large businesses, with annual growth expected to continue at a rate of close to 20% through 2027. In this context, it is important to note that 99% of cloud security breaches are expected to be the customer’s fault, according to Gartner.
The shared responsibility model for cloud services has been something that larger enterprises have been familiar with for some time already. Smaller organizations are, however, still coming to grips with this model. In respect of SaaS, this means that while the cloud provider is responsible for the application, SMBs are still adapting to the fact that they retain responsibility for their data and, crucially, manage their accounts and identities. Threat actors are, as a result, focusing on ways to compromise identities, especially using techniques such as credential stuffing and phishing.
Facing up to the Challenges of Hybrid IT
While SMBs were previously able to rely on antivirus software and firewalls to protect the technology assets on their premises, most have now moved into the world of hybrid IT as they increasingly rely on cloud-delivered services. While the security controls provided by most cloud services are good, SMBs face a variety of challenges in using the security functionality that is available to them.
As the attack surface of even smaller companies expands, the number of sources of security alerting grows. That is not the only challenge: threat actors will often not confine their activities to one part of your technology estate. They may start in one area, for instance, by compromising one or more endpoints (such as laptops) and then use the information they gather (such as credentials) to move laterally, for instance, to compromise a SaaS application. While large enterprises have spent the last 10 years or more building dedicated SecOps teams and intricate security toolchains, SMBs lack the resources for this kind of investment.
Democratizing Security Operations with XDR
What SMBs need is the ability to bring alerting from all of their IT infrastructure and applications into a single tool, which can analyze all of an organization’s telemetry, apply threat intelligence, and then provide a simple interface that acts as a single pane of glass for managing alerting, performing investigations and responding to threats. This is where XDR provides a solution that combines the key components of a traditional SecOps toolchain in a single cloud-hosted application, which can be delivered affordably. This is the second key area where NTTSH has turned its focus towards SMBs by focusing the development of its Samurai XDR product on the needs and budgets of SMBs while still delivering the functionality that large enterprises have become accustomed to. While GTIC’s research provides the intelligence needed to understand and detect the threats facing modern organizations, Samurai XDR makes GTIC’s work accessible and actionable even for organizations that lack dedicated SecOps resources. It is crucial to remember that while threat intelligence is essential to be able to detect threats, every organization needs tools in order to apply it.
A brief journey through Samurai XDR
From the start, Samurai XDR is designed to be easy to use and, most importantly, to be accessible to all IT staff, not only to security analysts. The starting point of all workflows in Samurai XDR is the alerts dashboard. This is where the system presents security alerts which have been prioritized based on severity and confidence.
 |
| Figure 3: Samurai XDR Alerts Dashboard |
The alerts dashboard brings together alerts from all of the technologies used by the organization into a single prioritized view, with a focus on providing an intuitive interface that can be used by most IT staff, not only by specialist security analysts.
Once the user has decided that an alert warrants further investigation, the Investigations view provides a similarly simple and intuitive interface for managing the lifecycle of an investigation of a potential security incident.
Once events and alerts are processed, they are stored in Samurai XDR’s data lake. The data lake provides the ability for users to query and analyze all of the events ingested into Samurai XDR, going back up to one full year. This makes it possible to interrogate a full year’s historical data for purposes such as threat hunting – allowing Samurai XDR users to perform detailed analyses of historical events for any signs of threats that may have been dwelling for longer periods of time. Querying the events in the data lake is made possible by Samurai XDR’s Advanced Query function, which allows users to search the data lake both graphically and using Microsoft’s Kusto Query Language (KQL).
Integrations
Integrations provide the mechanism to ingest telemetry (such as logs) from your IT infrastructure and applications into Samurai XDR. NTTSH has focused on bringing together the right mix of capabilities to ingest telemetry from both on-premises infrastructure and cloud services, mirroring the kind of hybrid IT environment that has become typical for even most SMBs today. Some examples of integrations currently available include:
- Cloud: Azure Management Plane and Microsoft 365 (coming soon), Google Workspace (coming soon)
- Endpoint Detection and Response: Microsoft Defender for Endpoint, VMWare Carbon Black and Crowdstrike Falcon Insight
- Next-Generation Firewalls: Cisco Secure Firewall (ASA and Firepower Threat Defense), Fortinet Fortigate, and Palo Alto Networks NGFW.
Over the coming months, NTTSH will be busy adding more integrations, including but not limited to Meraki, Bitdefender, Sophos, Zoom, MalwareBytes, OneLogin, OKTA, Zscaler, AWS, and many more!
Making it Easy
A key area of focus for NTTSH in the development of Samurai XDR has been that of making it easy to use and easy to afford. For example, the configuration of integrations is supported by simple “point and click” workflows. For infrastructure that provides logs via syslog, all that is needed is to point the log source at Samurai XDR’s secure syslog collector, and Samurai XDR will do the work of detecting the kind of device that is sending logs. Naturally, it’s the same for cloud integrations. Samurai XDR keeps the steps to a minimum and guides the user through interactive steps and access to knowledge-base articles.
Samurai XDR also follows a simple pricing model – based solely on the number of endpoints that the customer has, removing the need to try to estimate the data volumes of the telemetry that will be ingested into the platform. Standard pricing for 50 endpoints or more is only $3.33 per endpoint per month, and for smaller customers, there is a Starter Pack for up to 25 endpoints, which is priced at $750 for a year.
To make it easy to try out Samurai XDR, NTTSH is providing all new customers with a free 30-day trial, making it possible to experience all of its functionality without any commitments, giving even the smallest SMBs a risk-free route to building an advanced SecOps capability.
https://thehackernews.com/2024/02/why-we-must-democratize-cybersecurity.html



