A suspected Vietnamese-origin threat actor has been observed targeting victims in several Asian and Southeast Asian countries with malware designed to harvest valuable data since at least May 2023.
Cisco Talos is tracking the cluster under the name CoralRaider, describing it as financially motivated. Targets of the campaign include India, China, South Korea, Bangladesh, Pakistan, Indonesia, and Vietnam.
“This group focuses on stealing victims’ credentials, financial data, and social media accounts, including business and advertisement accounts,” security researchers Chetan Raghuprasad and Joey Chen said. “They use RotBot, a customized variant of Quasar RAT, and XClient stealer as payloads.”
Other commodity malware used by the group comprises a combination of remote access trojans and information stealers such as AsyncRAT, NetSupport RAT, and Rhadamanthys.
The targeting of business and advertisement accounts has been of particular focus for attackers operating out of Vietnam, with various stealer malware families like Ducktail, NodeStealer, and VietCredCare deployed to take control of the accounts for further monetization.
The modus operandi entails the use of Telegram to exfiltrate the stolen information from victim machines, which is then traded in underground markets to generate illicit revenues.
“CoralRaider operators are based in Vietnam, based on the actor messages in their Telegram C2 bot channels and language preference in naming their bots, PDB strings, and other Vietnamese words hard-coded in their payload binaries,” the researchers said.
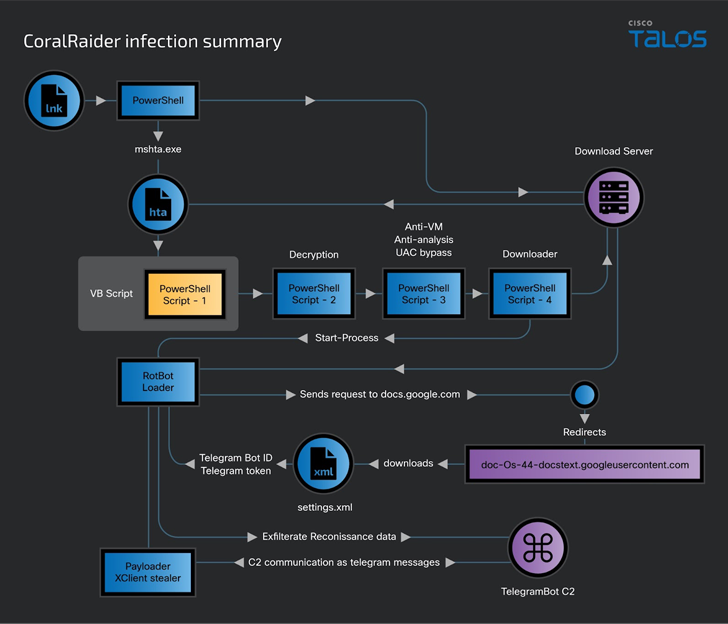
Attack chains start with a Windows shortcut file (LNK), although there is currently no clear explanation as to how these files are distributed to the targets.
Should the LNK file be opened, an HTML application (HTA) file is downloaded and executed from an attacker-controlled download server, which, in turn, runs an embedded Visual Basic script.
The script, for its part, decrypts and sequentially executes three other PowerShell scripts that are responsible for performing anti-VM and anti-analysis checks, circumventing Windows User Access Control (UAC), disabling Windows and application notifications, and downloading and running RotBot.
RotBot is configured to contact a Telegram bot and retrieve the XClient stealer malware and execute it in memory, ultimately facilitating the theft of cookies, credentials, and financial information from web browsers like Brave, Cốc Cốc, Google Chrome, Microsoft Edge, Mozilla Firefox, and Opera; Discord and Telegram data; and screenshots.
XClient is also engineered to siphon data from victims’ Facebook, Instagram, TikTok and YouTube accounts, gathering details about the payment methods and permissions associated with their Facebook business and ads accounts.
“RotBot is a variant of the Quasar RAT client that the threat actor has customized and compiled for this campaign,” the researchers said. “[XClient] has extensive information-stealing capability through its plugin module and various modules for performing remote administrative tasks.”
The development comes as Bitdefender disclosed details of a malvertising campaign on Facebook that’s taking advantage of the buzz surrounding generative AI tools to push an assortment of information stealers like Rilide, Vidar, IceRAT, and a new entrant known as Nova Stealer.
The starting point of the attack is the threat actor taking over an existing Facebook account and modifying its appearance to mimic well-known AI tools from Google, OpenAI, and Midjourney, and expanding their reach by running sponsored ads on the platform.
One is imposter page masquerading as Midjourney had 1.2 million followers before it was taken down on March 8, 2023. The threat actors managing the page were mainly from Vietnam, the U.S., Indonesia, the U.K., and Australia, among others.
“The malvertising campaigns have tremendous reach through Meta’s sponsored ad system and have actively been targeting European users from Germany, Poland, Italy, France, Belgium, Spain, the Netherlands, Romania, Sweden, and elsewhere,” the Romanian cybersecurity company said.
https://thehackernews.com/2024/04/vietnam-based-hackers-steal-financial.html